Recommanded Videos
![[18회] 개발 상담 - 질문도 용기다. 30분 리미티드(감기로 인해 30분만)](https://i1.ytimg.com/vi/TPtA0VyJarU/hqdefault.jpg)
[18회] 개발 상담 - 질문도 용기다. 30분 리미티드(감기로 인해 30분만)
2024. 12. 30.

스프링부트 개발자를 위한 유용한 VSCode 설정 팁
2025. 11. 11.

(눈은 쉬세요🙈) Go와 Rust 비교: 개발자를 위한 필수 가이드
2025. 5. 10.
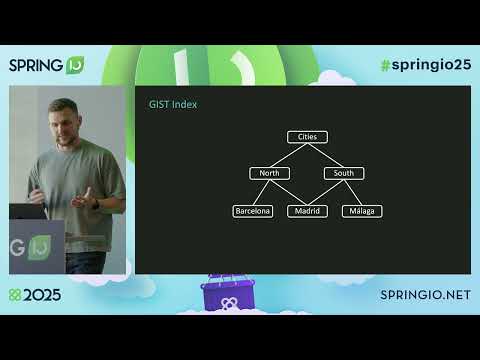
You don't need Elasticsearch! Fuzzy Search with PostgreSQL and Spring Data by Thomas Gräfenstein
2025. 9. 2.

100% Local Agents - DeepSeek R1 Agents with SmolAgents!
2025. 1. 21.

프로그래밍 언어 외우는 것인가 익숙해지는 것인가?
2025. 2. 6.